- Industrility
- Security
Security Whitepaper
Securing your Data is our Highest Priority
Security is priority zero for Industrility.
Industrility is committed to ensuring the safety and security of our customer and end-user data. We adhere to industry-standard privacy and security measures, as well as all applicable data privacy and security laws and regulations.
Industrility harnesses serverless technologies and managed services in AWS. This allows us to offload shared security responsibilities to AWS experts and leverage its massive engineering taskforce so we can stay laser-focus on delivering top-notch secure features to you.
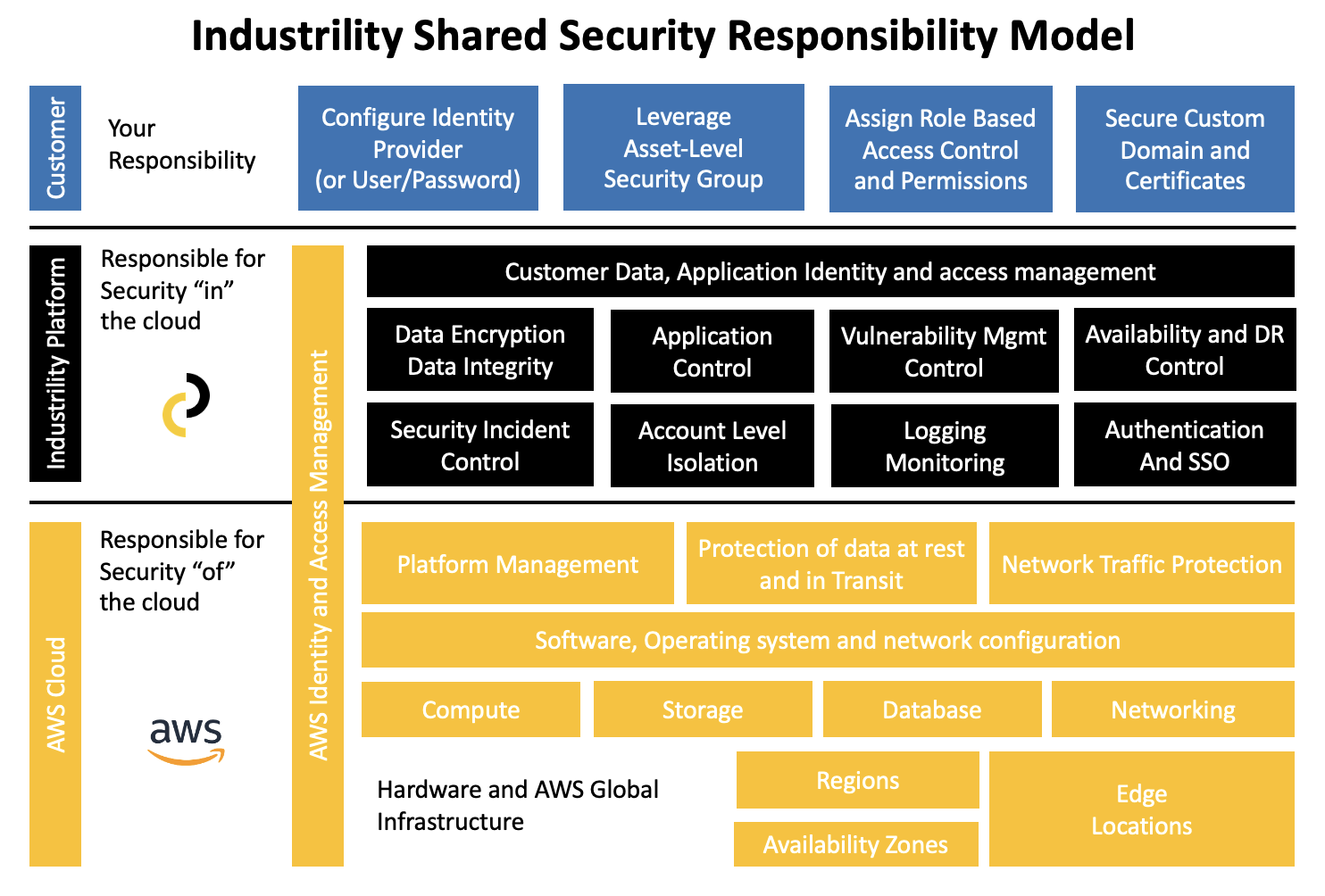
This whitepaper includes details of how we protect our systems and infrastructure against unauthorized or accidental access, loss, alteration, disclosure, or destruction. We have taken all necessary technical and operational measures to organize and protect our storage and networks, access controls, monitoring and logging, vulnerability and breach detection, and incident response measures.
Logging and Monitoring
We monitor and analyze information gathered from services and internal traffic in our network. We record this information in the form of event logs, audit logs, traffic logs, and virtual network traffic logs. These logs are automatically monitored and analyzed to a reasonable extent, which helps us identify anomalies such as unusual activity in employees’ accounts or attempts to perform malicious activities.
Data Protection Control
We follow industry best practices for Data Protection.
In-transit encryption: Industrility uses Transport Layer Security (TLS) 1.2 or above to encrypt all incoming HTTP traffic. This ensures that data transmitted between clients and servers is secure and protected from unauthorized access during transmission.
At-rest encryption: Industrility employs encryption techniques to protect data stored in databases, file systems, and other storage systems. This ensures that even if the data is compromised, it remains encrypted and unreadable to unauthorized users.
Key Management: Industrility has implemented robust key management practices to securely generate, store, and manage encryption keys. This includes measures such as key rotation, strong access controls, and secure storage of keys.
Ongoing monitoring and updates: Industrility regularly monitors the encryption mechanisms in place to identify any vulnerabilities or weaknesses. This allows for timely updates and improvements to ensure the ongoing security of data.
Access Control
Access control methods: Industrility follows industry best practices by implementing access control methods such as Role-Based Access Control (RBAC), where access is based on the roles and responsibilities of users within the organization. RBAC simplifies access control management by assigning permissions based on predefined roles, reducing the risk of unauthorized access.
Principle of Least Privilege: Industrility adheres to the principle of least privilege, ensuring that each user is granted only the specific privileges required for their role and no more. This minimizes the potential impact of a compromised account and limits unauthorized access to sensitive resources.
Network Security: We follow industry best practices for network security, including implementing firewalls (WAF), separate VPCs, and secure network protocols. Our network infrastructure is designed with segmentation and isolation to prevent unauthorized access and protect sensitive data. We enforce strong authentication mechanisms, such as multi-factor authentication, to ensure only authorized personnel can access our network resources.
Physical and Environmental Security: Industrility’s cloud infrastructure is securely hosted within Amazon Web Services (AWS), a leading public cloud provider. Benefits from the robust physical and environmental security measures provided by AWS. AWS is responsible for safeguarding our assets, ensuring they are housed in highly secure data centers.
Strong authentication measures: To protect against unauthorized access to administrative accounts, Industrility employs strong authentication protocols, such as multi-factor authentication (MFA). MFA adds an extra layer of security by requiring users to provide multiple factors of authentication, such as a password and a temporary code sent to their mobile device.
Separation of Environments: We implement the separation of development, testing, and operational environments protect the production environment and data from compromise by development and test activities. It helps with the segregation of duties and reduces the risk of unauthorized access to the live environment and data. It also allows for thorough testing of changes and new developments in a separate area before being deployed to the live operating environment.
Monitoring access logs: Industrility maintains access logs to track and monitor user activity. By analyzing access logs, Industrility can identify any suspicious or unauthorized access attempts and take appropriate actions to mitigate potential security risks.
Security Incident Control
At Industrility, we prioritize the security of our systems and data. To ensure the utmost protection against potential security incidents, we have implemented a comprehensive set of measures. These measures are designed to detect, prevent, and respond to any security incidents that may arise.
Incident Detection: Industrility has implemented a robust monitoring system that continuously scans and detects our infrastructure and systems for any suspicious activities or anomalies.
Incident Prevention: Our network infrastructure is protected by firewalls (WAF) and security groups that filter incoming and outgoing traffic, preventing unauthorized access and malicious attacks. Industrility also uses AWS managed serverless services which helps us stay on top of all security patches and updates.
Incident Response: In the event of a security incident, our team follows a well-defined incident response plan that outlines the necessary steps to contain, investigate, and mitigate the impact of the incident.
Vulnerability Management Control
We have a dedicated vulnerability management process that actively scans for security threats using security tools. Our security team monitors security reports to spot security incidents that might affect the company’s infrastructure. When we identify a vulnerability requiring remediation, it is logged, prioritized according to severity, and assigned to an owner.
Application Control
At Industrility, we implement a robust application control system to ensure the security of our assets. We adhere to the principle of complete mediation, forcing all requests through a common security “gatekeeper. In our platform, only users with the right asset security groups can see the assets (physical equipment).
Account-level isolation
Industrility App Platform is a multi-tenant environment and each tenant is represented using an account. Each account is isolated from other accounts and a user is associated with only 1 account. Data associated with one account, although stored in the shared databases, are isolated at various levels of security.
App-level Security for Users
Based on the number of “Apps” (modules) purchased by the customer, Each account has access to only specific apps. Users only gets access to the apps that they installed in their profile. Account admin can restrict which apps the user are allowed to install.
Asset-level Security Groups
By default, the users don’t have access to all the assets and the all the data associated with the asset. Administrators only give access to specific assets via Asset security groups. This limits data exposure and only authorized users have access to asset’s digital twin data.
Roles/Permissions
Using Role-based Access Control, each user is assigned a role. Each Role has Create, Read, Update, Delete Permissions defined for the given app. If the user does not have delete access for a given app, she cannot delete any resource within the app.
Availability Control
Business Continuity: Industrility, as a company, has implemented and follows business continuity practices to ensure the resilience of its operations. Business continuity is crucial for organizations to maintain their operations in the face of unexpected and disruptive incidents like natural disasters, cyberattacks, or pandemics. At Industrility, we understand the importance of maintaining business continuity even in challenging circumstances. We have implemented robust business continuity management practices to ensure the resilience of our operations. Our approach includes aligning our Business Continuity Policy with our strategic direction, integrating the Business Continuity Management System (BCMS) into our business processes, and allocating the necessary resources to support it.
High Availability Infrastructure: Industrility strives to create a high availability infrastructure that combines hardware, software, and applications designed to recover quickly in the event of outages.
Fault Tolerance: Fault tolerance is another important aspect of Industrility’s infrastructure. By designing systems with fault tolerance in mind, Industrility aims to minimize the impact of failures and ensure the continuity of operations. This is achieved through following practices such as utilizing secondary sites to fail-over and implementing site-to-site failover configurations.
Development Best Practices
Industrility follows development best practices to enhance availability control. Some of these practices include:
- Proper change management processes.
- Industrility actively monitors the health of its applications and infrastructure components.
- Industrility ensures proper change processes and controls are in place for network and firewall changes, making incremental changes and validating each change to minimize risk.
Backup
Industrility follows industry best practices to implement backups, Industrility runs backups for databases frequently, and backups are stored securely in primary as well as secondary regions. All backups are scheduled and tracked regularly. In the event of a failure, a re-run is initiated and fixed immediately. All backed-up data is retained for a period of thirty days.
Customer Security Controls
So far, we’ve covered the measures we take to provide security on various fronts for our customers. Here are some actions you can take to ensure your security:
- Select a strong, unique password, and keep it secure.
- Implement multi-factor authentication.
- Be mindful when sharing data from our cloud environment and only share necessary information.
- Regularly monitor devices linked to your account, active web sessions, and third-party access to identify any unusual activities and manage your account roles and privileges.
- Stay alert to phishing and malware threats by being wary of unfamiliar emails, websites, and links that may misrepresent Zoho or other trusted services to exploit your sensitive information.
- Categorize your information as personal or sensitive and label it accordingly.
- Keep your browser, mobile OS, and applications updated to ensure they are patched against vulnerabilities and can utilize the latest security features.
Conclusion
At Industrility, ensuring the security of your data is at the core of everything we do. We prioritize the security of your information in every aspect of our operations, from our infrastructure to our products and the actions of our personnel. Our commitment to data protection is unwavering, and we continually strive to implement best practices and the latest security measures to guarantee your data remains safe and confidential. Your trust in us is of utmost importance, and we work tirelessly to earn and maintain it by upholding the highest standards of data security.
SOC2 Certification: Request Report
AWS Well-Architected Framework Review: Contact us


